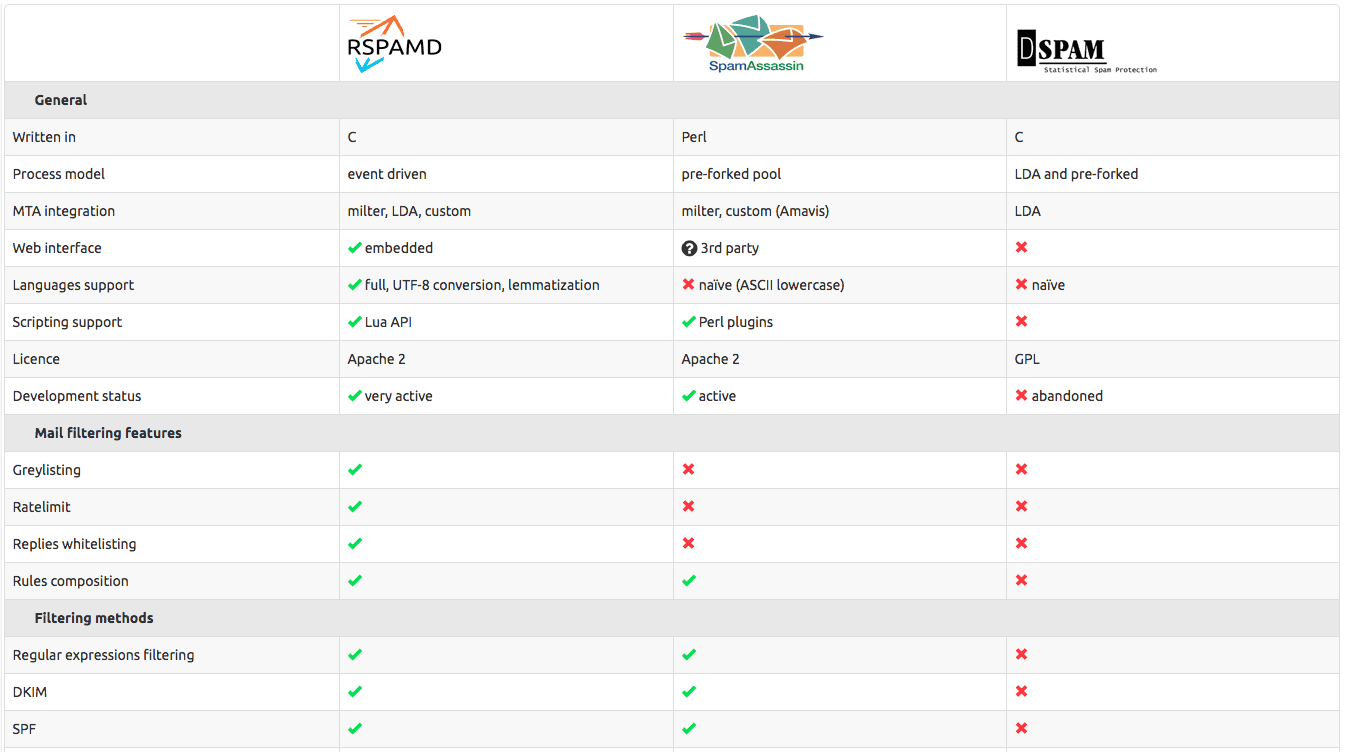
rspamd is a replacement of spamassassin, with more efficient resource utilization.
https://gist.github.com/mdpuma/f1c347091717240276fcb0bab737f7ec
this is the Gist, on how to integrate it on cpanel, by changing Exim configuration.
rspamd is a replacement of spamassassin, with more efficient resource utilization.

https://gist.github.com/mdpuma/f1c347091717240276fcb0bab737f7ec
this is the Gist, on how to integrate it on cpanel, by changing Exim configuration.
Afterlogic have some interesting new look to the webmail of cpanel. Guides available at https://afterlogic.com/docs/webmail-lite/installation/install-on-cpanel
cd /root/
wget https://afterlogic.com/download/webmail-panel-installer.tar.gz
tar -xzvf ./webmail-panel-installer.tar.gz
cd ./webmail-panel-installer
chmod a+x ./installer
./installer -t lite -a install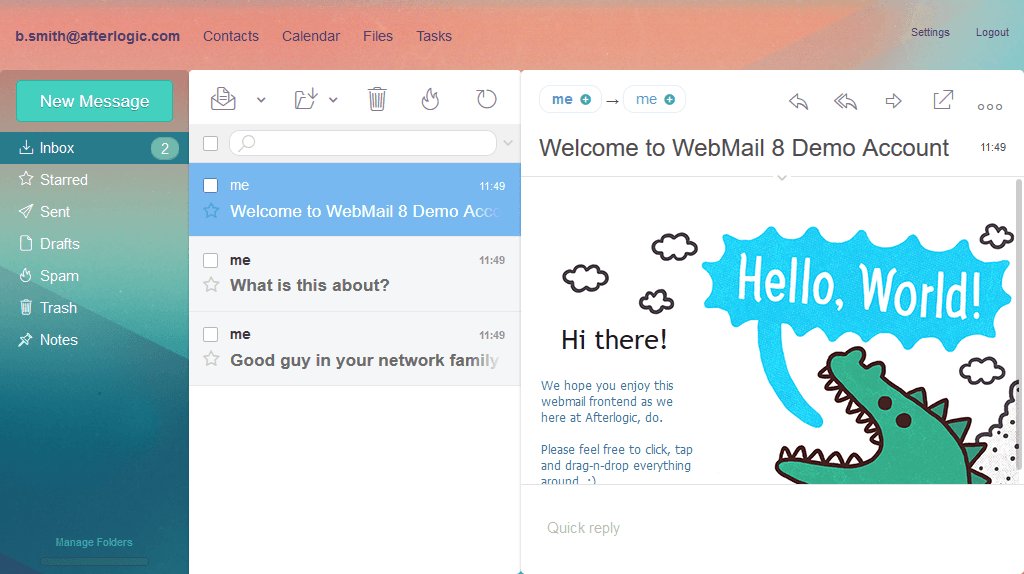
Tools
– head for Chrome (ElasticSearch Head – Chrome Web Store)
– Postman (link)
– Insomenia (link)
– elasticdump – nodejs (link)
Monitoring
– ps_mem.py – monitor real memory utilization (github link)
– ps -eo size,pid,user,command --sort -size | awk '{ hr=$1/1024 ; printf("%13.2f Mb ",hr) } { for ( x=4 ; x< =NF ; x++ ) { printf("%s ",$x) } print "" }' |cut -d "" -f2 | cut -d "-" -f1 | head -n 40
from : here
– netdata, dockerable too – (link)
System tuning
sysctl -w vm.max_map_count=262144
sysctl -w vm.swappiness = 0
verify
sysctl vm.max_map_count
sysctl vm.swappiness
Reference
https://stefanprodan.com/2016/elasticsearch-cluster-with-docker/
Memory tuning
https://qbox.io/blog/memory-considerations-in-elasticsearch-deployment
https://plumbr.io/handbook/gc-tuning-in-practice
Stuck shards
https://thoughts.t37.net/how-to-fix-your-elasticsearch-cluster-stuck-in-initializing-shards-mode-ce196e20ba95
https://www.datadoghq.com/blog/elasticsearch-unassigned-shards/
elasticdump (link)
# Backup index data to a file:
elasticdump \
--input=http://production.es.com:9200/my_index \
--output=/data/my_index_mapping.json \
--type=mapping
elasticdump \
--input=http://production.es.com:9200/my_index \
--output=/data/my_index.json \
--type=data
# Backup and index to a gzip using stdout:
elasticdump \
--input=http://production.es.com:9200/my_index \
--output=$ \
| gzip > /data/my_index.json.gz
Export elasticsearch to csv (link)
docker pull nimmis/java-centos:oracle-8-jdk
wget https://artifacts.elastic.co/downloads/logstash/logstash-7.1.1.tar.gz
tar zxf logstash-7.1.1.tar.gz
ln -s logstash-7.1.1 logstash
docker run -ti -d --name logstash -v `pwd`/logstash:/home/logstash nimmis/java-centos:oracle-8-jdk
docker exec logstash /home/logstash/bin/logstash-plugin install logstash-input-elasticsearch
docker exec logstash /home/logstash/bin/logstash-plugin install logstash-output-csv
Put this into `pwd`/logstash/export-csv.conf
input {
elasticsearch {
hosts => "elastic:9200"
index => "datafeed"
query => '
{
"query": {
"match_all": {}
}
}
'
}
}
output {
csv {
# elastic field name
fields => ["field1", "field2", "field3", "field4", "field5"]
# This is path where we store output.
path => "/home/logstash/exported-data.csv"
}
}
filter {
mutate {
convert => {
"lat" => "float"
"lon" => "float"
"weight" => "float"
}
}
}
./bin/logstash -f /home/logstash/export-csv.conf
#!/bin/bash
# This is PER TABLE backup. Each table will be backed up individually
## to enable passwordless mysqdump, put your password in /etc/mysql/[mysqld|percona|maria].conf.d/client.conf
# [client]
# user=""
# pass=""
THEDB="mydbname" # THE DATABASE
OUTPUT="/home/backup/mysqldump"
DATE=`date +%Y%m%d`
OPTS="--max_allowed_packet=512M "
tables=`mysql -e "use $THEDB; show tables;" | tr -d "| " | grep -v -E "^Tables_in_" `
mkdir -p $OUTPUT/$THEDB-$DATE
for table in $tables; do
STAGEDDATE=`date +%Y%m%d`
echo "Dumping table : " $table
mysqldump -a $OPTS $THEDB $table > $OUTPUT/$THEDB-$DATE/$STAGEDDATE-$table.sql
gzip $OUTPUT/$THEDB-$DATE/$STAGEDDATE-$table.sql
done
echo "Backup done at " $OUTPUT/$THEDB-$DATE
Key points
Enable http2
On apache + prefork to event – https://techwombat.com/enable-http2-apache-ubuntu-16-04/
sudo add-apt-repository ppa:ondrej/apache2sudo apt updatesudo apt upgradesudo apt install php7.0-fpmsudo a2enmod proxy_fcgi setenvifsudo a2enconf php7.0-fpmsudo a2dismod php7.0
sudo a2dismod mpm_preforksudo a2enmod mpm_eventsudo service apache2 restartsudo service php7.0-fpm restart
Add in <VirtualHost>… </VirtualHost> for individual site, or in apache.conf file, for global settings.
Protocols h2 h2c http/1.1sudo a2enmod http2
sudo service apache2 restart
Nginx – Need to compile nginx with http2 module
./configure –with-compat –add-dynamic-module=../ModSecurity-nginx –with-http_ssl_module –with-stream_ssl_module –prefix=/etc/nginx –with-http_v2_module
** mod_security for nginx, follow this : https://www.nginx.com/blog/compiling-and-installing-modsecurity-for-open-source-nginx/
This post content is under development.. new content will be added in the future.
Useful links
Elasticdump – http://blog.ruanbekker.com/blog/2017/11/22/using-elasticdump-to-backup-elasticsearch-indexes-to-json/
sudo npm install n -gsudo n stable
Delete by time https://hobo.house/2016/02/18/how-to-manually-clean-indexes-from-elasticsearch/
I have additional services need to be monitored. Such as snmpd
http://thecpaneladmin.com/adding-services-to-chksrvd-for-monitoring/
add a file /etc/chkserv.d/snmpd
add this content.
service[snmpd]=x,x,x,systemctl restart snmpd.service,snmpd,root
Restart chkservd
/scripts/restartsrv_chkservd
This happens all the times to me. Keeping a note here..
for Centos
https://www.noreplied.com/how-to-fixed-cannot-change-locale-utf-8-error-in-centos-7/
cat 'LC_CTYPE="en_US.UTF-8"' >> /etc/environment
For Ubuntu
export LANGUAGE=en_US.UTF-8
export LANG=en_US.UTF-8
export LC_ALL=en_US.UTF-8
locale-gen en_US.UTF-8 en_US
dpkg-reconfigure locales ->> choose 149 and 3
What it is
https://en.wikipedia.org/wiki/Slowloris_(computer_security)
Tools to check
Slowloris : https://github.com/gkbrk/slowloris
SlowHttpTest : https://github.com/shekyan/slowhttptest
mod_qos
apt-get update && apt-get -y install libapache2-mod-qos && a2enmod qos && /etc/init.d/apache2 restart
* configuration file in /etc/apache2/mods-enabled/
mod_reqtimeout
a2enmod reqtimeout && /etc/init.d/apache2 restart
* configuration file in /etc/apache2/mods-enabled/
Some notes on securing apache..
A few key points
Disable access to .
https://stackoverflow.com/questions/4352737/apache-configuration-regex-to-disable-access-to-files-directories-beginning-wit
<filesmatch "^\.ht">
Order allow,deny
Deny from all
<filesmatch “^\.”>
Order allow,deny
Deny from all
<directorymatch “^\.|\/\.”>
Order allow,deny
Deny from all
Disable banner
http://www.ducea.com/2006/06/15/apache-tips-tricks-hide-apache-software-version/
Usually found in /etc/apache/conf-enabled/security.conf
Disable PHP functions
https://www.cyberciti.biz/faq/linux-unix-apache-lighttpd-phpini-disable-functions/
disable_functions =exec,passthru,shell_exec,system,proc_open,popen,pcntl_exec,curl_exec,curl_multi_exec,parse_ini_file,show_source,phpinfo,eval,assert,create_function
Slow DOS mitigation
http://www.farhanfaisal.com/slow-http-dos-verify-and-mitigate/