I bet most of us still do not have the idea of rising internet threats nowadays. It seems irony, as everyone goes online and relying their business to the internet, they still tend to be the victim, and become part of the darkside of the internet without them knowing.
One scenario that we might think about, my computer have been infected with virus, but I still can send my email as usual. So, whats the deal? Well, there’s a lot more about the virus that you dont know. We’ll just discussed about 2 issues here, banking trojan like zeus, and also botnet.
Zeus trojan
Zeus trojan is a banking centric trojan, where it steals banking information by keylogging. There quite a number of infection nowadays, and thousands of variants. Zeus package were sold for anyone to run the botnet. The package comes with the virus builder, that were custom made for your configurations. So, your banking information might not be received by one person. Anyone could steal your banking information. The data will be submitted to Command and Control (CnC) server, specified by the creator.
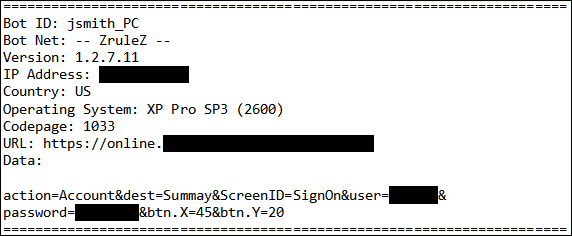
Picture from http://www.secureworks.com/research/threats/zeus/?threat=zeus, showing what kind information being stealed
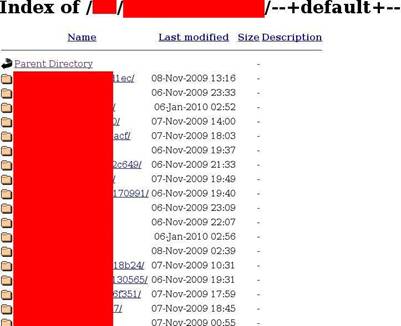
Picture from http://www.secureworks.com/research/threats/zeus/?threat=zeus, showing sample collection of data on CnC server
To see how serious it is, please visit this page. Zeus Tracker. Zeus tracker is a project where all detected hosted zeus malware, and the CnC in all countries were placed in a repository. You can limit your search by country, and ASN. If you want to understand further what zeus trojan did on infected computer, SecureWorks have come out with a comprehensive report on zeus trojan. All information about the market place, sample data stolen, screenshot of CnC interface, and additional zeus trojan module, which enhance its capability of stealing data.
For ISP and network administrator who manage a big network and bunch of IP addresses, you can search for CnC and hosted zeus binaries in your network by country, or ASN. Besides that, you can retrieve those information through RSS feed. With a simple RSS reader, you can get latest information about zeus threats in your network. And besides zeus trojan, there are more feed provider that could give you such information, such as similar project, Spyeye tracker, which monitor Cnc and hosted spyeye malware. Have a look on conficker and others as well from shadowserver.
Botnet
Botnet in this case means a network of drones, remote controlled computer harnessed by malware and command and control. Usually infected computers will connect to CnC server specified, either hardcoded, algorithmically generated or over fast-flux. Once your computer have been infected, you might be within the bot network (botnet), which able to receive commands from the bot herder (botnet owner). One of the most popular botnet is Conficker, with its unique way of choosing CnC, which were algorithmically generated everyday.
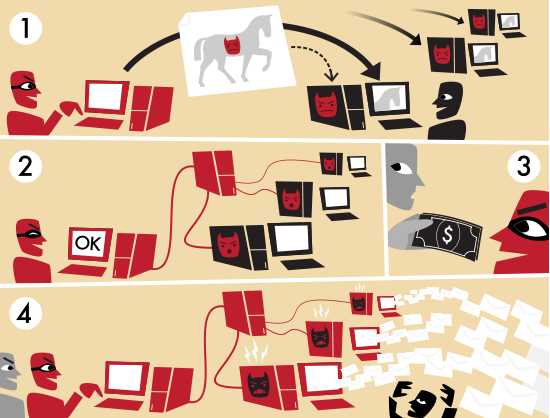
Picture from Wikipedia:Botnet
The image below illustrate the bot herder, sending spam email from the botnet for money. We should not limit it to spamming only. There’s a whole new business model with botnet, such as botnet for rent, DDOS, phishing, and bunch of other internet threats. Here’s a bunch of uses of botnet by Honeynet Project. So, your infected computer might be doing some of the function listed there. Which one, check it yourself. How big it can be, check this out. Kneber or BTN1, infected about 75,000 system within a year and a half. Thats quite a big number.
Talking about Conficker, Felix Leder and Tillmann Werner have come out with comprehensive analysis of Conficker, and how to detect and mitigate them. They even wrote a tool that could generate the possible generated domains for CnC for a particular day called Downatool2. The approach described will give an insight on how to mitigate them, in a large organizational network that possibly infected with Conficker.
For starters, just check your computer for malware infection. ConfickerWorkingGroup have came out with Conficker eye chart to detect whether you have been infected with conficker, and even its possible variant. And yes, Conficker comes in a few variants. Besides that, just scan your computer with MalwareBytes, for any sign of infection. If you think you’re abit more adventurous than that, run HijackThis, and submit the output to Hijackthis log analyzer such as one from exelib.com or hijackthis.de. If its not enough, maybe you can start by reading this article by Symantec, Malware Analysis for Administrators.